There has never been a more pressing need for effective data security in a world where digital communication and information exchange have become standard. A new era of security is about to begin as traditional cryptographic techniques face growing threats from potent computing systems and sophisticated attacks: quantum cryptography. With the help of quantum mechanics, uncrackable encryption techniques have been developed, offering previously unimaginable levels of data security. In this thorough investigation, we explore the world of quantum cryptography, including its fundamental ideas, potential uses, difficulties, and opportunities.
What is Quantum Cryptography?
Encrypting data, or turning plain text into scrambled text, allows only those with the proper “key” to decode it and read the data. By extension, quantum cryptography is just the encryption and secure transmission of data using the ideas of quantum mechanics.
Although the definition appears straightforward, the complexity of quantum cryptography lies in the fundamental ideas of quantum mechanics, such as:
- The universe’s constituent particles are inherently ambiguous and capable of existing in multiple locations or states at once.
- There are two quantum states in which photons can be generated at random.
- A quantum property cannot be measured without being altered or disturbed.
- A particle’s quantum properties can be duplicated, but not the entire particle.
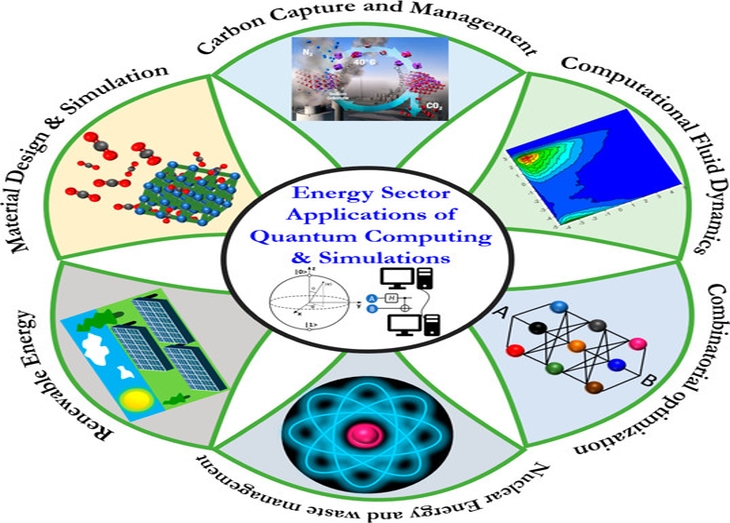
How Quantum Cryptography Works
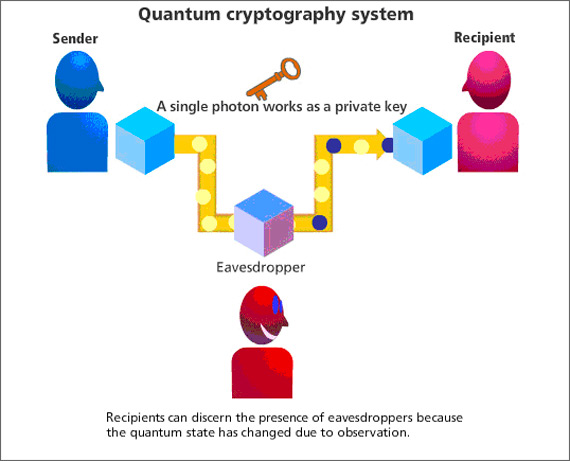
Data is transmitted from one location to another over a fiber optic cable using a series of photons (light particles) in quantum cryptography, also known as quantum key distribution (QKD). The two endpoints can figure out what the key is and whether it is secure to use by comparing measurements of the characteristics of a fraction of these photons.
- Photons are transmitted by the sender through a filter (or polarizer) that assigns them one of four possible polarizations and bit designations at random: vertical (one bit), horizontal (zero bit), 45 degrees to the right (one bit), or 45 degrees to the left (zero bit).
- The photons arrive at a receiver, where two beam splitters, one horizontal/vertical and one diagonal, are used to “read” the polarization of each individual photon. In order to determine which beam splitter to use for each photon, the receiver must make a guess.
- The sender uses a beam splitter to send photons, and the receiver determines the correct splitter for each photon. The sender compares this information with the polarizer sequence, discarding incorrectly read photons and generating the key.
Quantum cryptography principles
Secure communication is made possible by quantum cryptography, which makes use of the ideas behind quantum mechanics, a branch of physics that examines the behavior of subatomic particles. Traditional cryptography relies on mathematical calculations for both encryption and decryption. In contrast, quantum cryptography transmits data securely by utilizing the characteristics of photons, which are light-related particles.
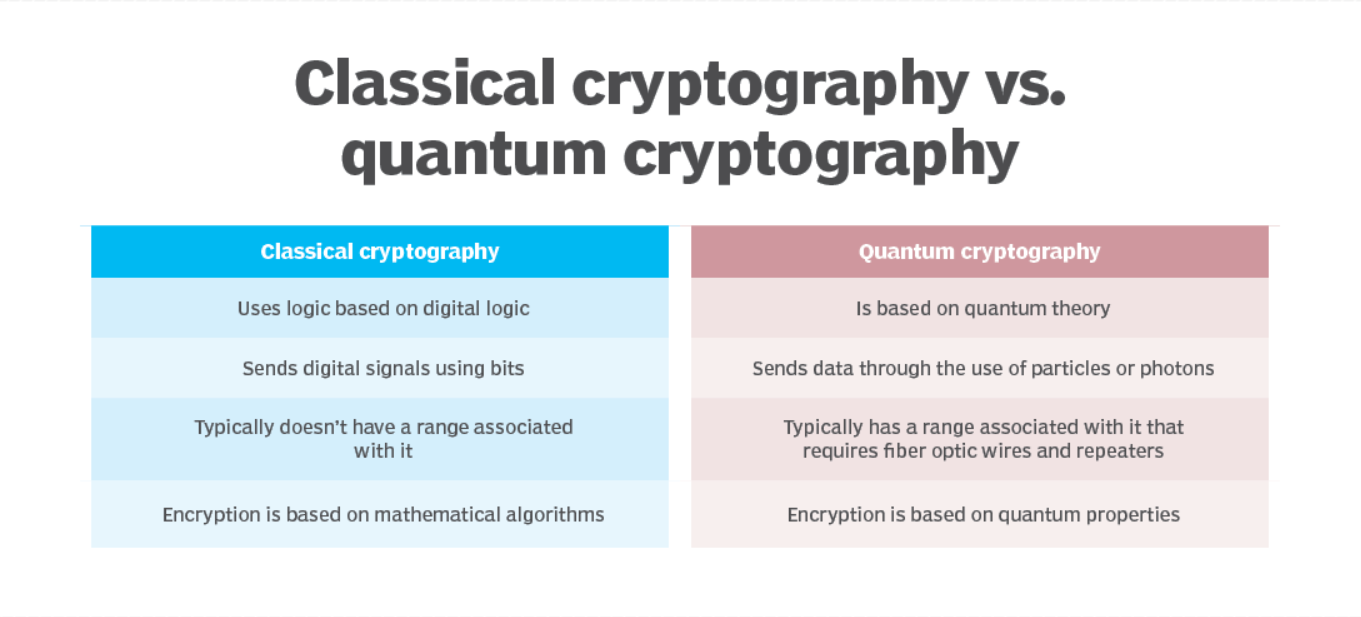
Quantum vs. Conventional Cryptography
Quantum cryptography is fundamentally different from conventional cryptography in that it permits the transmission of data that, in theory, is impossible to intercept or eavesdrop on without being noticed. This is because it is impossible for an attacker to copy or intercept the information without being noticed because photons can exist in multiple states simultaneously, a concept known as superposition.
Two Steps to Transmitting Information
In quantum cryptography, two main steps are key distribution and message transmission. Key distribution involves two parties exchanging photons to establish a cryptographic key that is detectable by the parties involved. The key is then used to encrypt and decrypt messages, ensuring secure communication. The use of photons prevents the loss of information and ensures that any attempt to copy or measure photons in transit is detected.
Action of Quantum Cryptography
A number of protocols are included in quantum cryptography that aim to achieve secure communication. Let’s examine a few of the popular quantum cryptographic techniques:
- (QKD) Quantum Key Distribution: QKD protocols, like the well-known BB84 protocol, let two parties exchange encryption keys in a secure manner over an insecure channel. Quantum mechanics’ principles provide the security behind QKD, making it nearly impossible for someone listening in to intercept the keys without being noticed.
- Signatures in quantum technology: Quantum digital signatures make use of the properties of the quantum world to produce tamper-evident signatures. The quantum states will be disturbed by any attempt to change the signature, making it detectable.
- Quantum cryptography: Cryptography could undergo a quantum computer revolution, either favorably or unfavorably. Although quantum cryptography provides unbreakable security, classical cryptographic techniques may be compromised by quantum computers, necessitating the development of quantum-safe cryptographic algorithms.
- Exchange of quantum keys: Entanglement is used by quantum key exchange protocols, such as the Ekert protocol (E91), to create a shared secret key between two parties. This key can then be used with conventional cryptographic techniques for safe communication.
Applications of Quantum Cryptography in the Real World
By offering unmatched data security, quantum cryptography has the potential to revolutionize many different industries and sectors. The following are some of the most promising applications:
- Protection of Critical Infrastructure: Society depends on transportation networks, water supplies, and power grids. These infrastructures’ security can be strengthened through quantum cryptography, guarding against disruptions and cyberattacks.
- Discreet Communications: Governments, companies, and individuals can all benefit from secure communication channels offered by quantum cryptography. Sensitive data can be transmitted with confidence, including financial transactions and classified information.
- Security for the Internet of Things (IoT): The importance of secure device communication increases as the IoT grows. For IoT networks, quantum cryptography can offer an impenetrable layer of security.
- Government and military communications: For military operations and the sharing of classified information, secure communication channels are necessary for national security. Even the most sophisticated attacks may not be able to breach quantum cryptography’s level of security.
- Financial Services: Quantum cryptography can help the financial sector secure sensitive customer data, protect transactions, and stop fraud.
- Management of Identity and Authentication: Systems for identity management and authentication can benefit from quantum cryptography. Cryptographic algorithms that are quantum-resistant can be used to protect digital identities, stop identity fraud, and guarantee the reliability of user authentication procedures.
Getting Past Obstacles in Quantum Cryptography
Although quantum cryptography has ground-breaking potential, it also faces formidable obstacles:
- Technical Difficulty: Quantum cryptography requires specialized infrastructure, including quantum key distribution (QKD) systems, as well as sophisticated technologies. The current cost and difficulty of scaling these systems prevent their wide-scale adoption. The future of quantum cryptography will depend on overcoming these technical obstacles and creating more affordable, scalable solutions.
- Infrastructure and Standards: For quantum cryptography to be widely adopted, it is crucial to establish a solid infrastructure and standardized protocols. Currently, there is a need for standardized protocols that ensure interoperability and compatibility between different quantum cryptographic systems. Developing these standards will necessitate cooperation among researchers, industry stakeholders, and regulatory bodies.
- Quantum Computing Development: Quantum computers can break cryptographic algorithms, making quantum-resistant encryption crucial for future communication security. Researchers are working on post-quantum cryptography, focusing on encryption methods that withstand quantum attacks.
- Integration with Existing Systems: Integrating quantum cryptography into communication systems requires infrastructure modifications and protocol compatibility, ensuring a smooth transition and practical implementation.
- Education and Awareness: Professionals, decision-makers, and end users need to be educated and made aware of the highly specialized nature of quantum cryptography. For quantum cryptography to be successfully adopted in different industries and daily life, it will be crucial to promote understanding of the technology’s advantages and limitations.
- Distance Restriction: The maximum distance over which entanglement can be maintained restricts entanglement-based quantum cryptography. The development of techniques for long-distance quantum communication is currently underway.
Quantum Cryptography’s Future
Quantum cryptography has a promising future, with ongoing research and technological developments poised to get around current restrictions and spur adoption:
- Quantum Internet: Often referred to as the “quantum internet,” a quantum internet is a hypothetical global network that uses quantum cryptography to ensure secure communication between users.
- Quantum repeaters: The secret to increasing the range of secure quantum communication is the use of quantum repeaters. Entanglement signals can be amplified and refreshed by these devices, allowing for long-distance quantum key distribution.
- Quantum Networks: Interconnected quantum devices will be made possible by the development of quantum networks, enabling secure communication between numerous nodes and locations.
- Technological Developments: Quantum cryptography will become more widely used and practical as a result of developments in quantum hardware, error correction, and quantum memory.
Data security is about to undergo a revolution thanks to quantum cryptography, which provides a level of security that was previously thought to be unattainable. Superposition and entanglement, two concepts from quantum mechanics, have paved the way for uncrackable encryption techniques that can fend off even the most complex assaults. Despite difficulties, ongoing research and technological development are advancing quantum cryptography toward widespread application and practical implementation. The potential of quantum cryptography to reshape industries, safeguard sensitive information, and ensure a more secure digital future is both remarkable and promising as we stand on the threshold of a new era in security.